Investigating real-life smishing attempts
Smishing Chronicles: The Mauritius Post Phishing Scam¶
From the Desk of a Cyber Sleuth¶
Ah, another day, another smishing attempt. This time, our friendly neighborhood scammers have tried to impersonate Mauritius Post with a message so full of red flags that even a colorblind person would be suspicious.
Suspicious Smishing Attempt – The Initial Clues¶
From Address:¶
usy3edsusyeds6@aol.com
mauritiuspost.mu domain and thought AOL was the way forward. Sure, Jan.
The Message¶
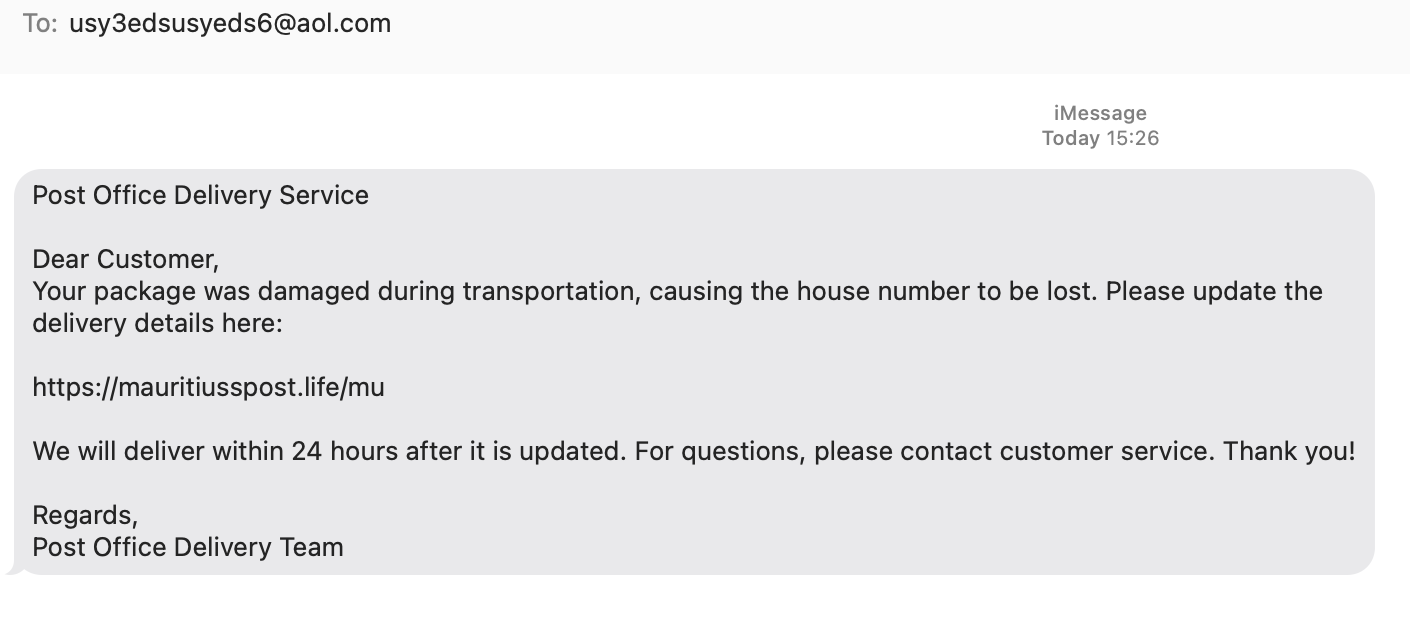
A classic urgency-based social engineering move:
"Your package is damaged! Quick, update your details or the mail fairy will make it disappear forever!"
Panic-inducing, poorly phrased, and with an obviously suspicious typosquatted domain (mauritiusspost.life).
Level 1 Technical Analysis – Let's Whois This Thing¶
Running a WHOIS query on the domain:
whois mauritiusspost.life
Command Output:¶
Domain Name: mauritiusspost.life
Registry Domain ID: 47df6ab0031949699af4b0bc2946c715-DONUTS
Registrar WHOIS Server: whois.namesilo.com
Registrar URL: https://www.namesilo.com/
Creation Date: 2025-02-25T07:00:00Z
Updated Date: 2025-02-25T07:00:00Z
Registrar Registration Expiration Date: 2026-02-25T07:00:00Z
Registrar: NameSilo, LLC
Registrar IANA ID: 1479
Domain Status: clientTransferProhibited https://www.icann.org/epp#clientTransferProhibited
Name Server: RANDY.NS.CLOUDFLARE.COM
Name Server: SHUBHI.NS.CLOUDFLARE.COM
Key Findings:¶
✅ Domain registered literally a day ago – Freshly baked phishing attempt!
✅ Privacy-protected WHOIS – Because why make it easy for law enforcement?
✅ Cloudflare DNS – Smart move, scammers. Makes takedown slightly harder.
This is TLD swapping + Typosquatting at its best. Instead of mauritiuspost.mu, they use mauritiusspost.life. Just enough to trick someone into clicking, but obvious to the trained eye.
Level 2 Technical Analysis – The Fake Website Hunt¶
First Attempt: Desktop Browser Access¶
curl -I https://mauritiusspost.life/mu
Command Output:¶
HTTP/2 404
date: Wed, 26 Feb 2025 19:45:49 GMT
content-type: text/plain; charset=utf-8
server: cloudflare
Huh, a 404? Surely the scammers didn't set up a phishing page and then forget about it? Or did they?
Second Attempt: Spoofing a Mobile Browser¶
curl -A "Mozilla/5.0 (iPhone; CPU iPhone OS 15_0 like Mac OS X) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Mobile Safari/537.36" -I https://mauritiusspost.life/mu
Command Output:¶
HTTP/2 200
date: Wed, 26 Feb 2025 19:52:53 GMT
content-type: text/html; charset=utf-8
server: cloudflare
Digging Deeper: Stealing the Scam Website’s Files¶
Let's analyse the phishing page structure¶
root@LakazMama:/home/renwa/Desktop/Malware_Analysis/260225_smishing# curl -A "Mozilla/5.0 (iPhone; CPU iPhone OS 15_0 like Mac OS X) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Mobile Safari/537.36" https://mauritiusspost.life/mu -o phishing_page.html
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 452 0 452 0 0 605 0 --:--:-- --:--:-- --:--:-- 606
root@LakazMama:/home/renwa/Desktop/Malware_Analysis/260225_smishing#
root@LakazMama:/home/renwa/Desktop/Malware_Analysis/260225_smishing# ls
phishing_page.html
root@LakazMama:/home/renwa/Desktop/Malware_Analysis/260225_smishing# cat phishing_page.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<link rel="icon" href="/mus_post/140.png">
<meta name="viewport" content="width=device-width, initial-scale=1.0, user-scalable=no">
<title>Mauritius Post Ltd, more than just letters</title>
<script type="module" crossorigin src="/assets/index-cae35c69.js"></script>
<link rel="stylesheet" href="/assets/index-8036a4cf.css">
</head>
<body>
<div id="app"></div>
</body>
</html>
root@LakazMama:/home/renwa/Desktop/Malware_Analysis/260225_smishing#
Wget Magic – Grabbing the Whole Site¶
wget -r --no-parent -U "Mozilla/5.0 (iPhone; CPU iPhone OS 15_0 like Mac OS X) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Mobile Safari/537.36" -P phishing_site --adjust-extension https://mauritiusspost.life/mu
.
└── phishing_site
└── mauritiusspost.life
├── assets
│ ├── index-8036a4cf.css
│ └── index-cae35c69.js
├── mu.html
└── mus_post
├── 140.png
└── assets
├── 53ac32dcwSnsQ.png
├── 918b7dc3wSnsQ.woff2
└── f31b8056wSnsQ.woff2
6 directories, 7 files
mu.html is just a loader page. The real action happens inside index-cae35c69.js.
The JavaScript Scam Script – Show Me the Money¶
Inside index-cae35c69.js, we find some juicy phishing logic:
{
"For redelivery": "For redelivery, we need to charge some service fees.Your package will be re-delivered after payment",
"lump sum: ": "lump sum: ",
Cardholder: "Cardholder",
"Card Number": "Card Number",
"Expire Date": "Expire Date",
"Security Code": "Security Code",
Submit: "Submit",
"Click here to receive another code": "Click here to receive another code",
"Please confirm your identity and a one-time code will be sent": "Please confirm your identity and a one-time code will be sent to your mobile number or email address. Please enter verification code here",
"The verification code has been sent to": "The verification code has been sent to",
"Please do not click the": "Please do not click the 'Refresh' or 'Back' buttons as this may terminate or terminate your transaction",
"Verification code error, please try again": "Verification code error, please try again",
"The session is about to expire, please complete the verification now": "The session is about to expire, please complete the verification now",
"This card does not support this transaction, please try another card": "This card does not support this transaction, please try another card",
"Authorized bank": "Authorized bank",
"Please go to the bank App to confirm the authorization": "Please go to the bank App to confirm the authorization",
"Please do not close this page": "Please do not close this page",
"Payment Successful": "Payment Successful!",
"Thank you for your purchase. Your payment has been processed successfully": "Thank you for your purchase. Your payment has been processed successfully",
"Mailing address": "Mailing address",
"street address or house number": "street address or house number",
"Apartment number": "Apartment number, room number, etc.",
"Safe payment": "Safe payment",
"Verification code": "Verification code",
"Delivery status": "Delivery status",
"Your package number": "Your package number: {0}",
"Failure notice of delivery": "Failure notice of delivery",
"Because the delivery address is not clear, your package is not delivered": "Because the delivery address is not clear, your package is not delivered",
"Your package has returned to our operation center": "Your package has returned to our operation center",
"Please update your address": "Please update your address, we will ship again in {0}",
Continue: "Continue",
"Next Step": "Next Step",
"Update Immediately": "Update Immediately",
"Online Payment": "Online Payment"
}
- Credit Card Info (Number, Expiry, CVV)
- 2FA / OTP Verification (to bypass security checks)
- Fake payment confirmation (likely rerouted to the scammer's account)
A multi-stage phishing attack: 1. Collect personal data 2. Steal credit card details 3. Simulate a bank verification step 4. Profit 💰
Conclusion – Lessons Learned¶
🎭 Scammers are getting craftier, but we are smarter. - TLD Swapping + Typosquatting is still a favorite phishing trick. - Mobile-specific attacks are increasing. - Social engineering works—urgency and fake delivery scams can fool people. - Privacy-protected domains + Cloudflare make takedowns harder.
🛡 How to Stay Safe:
✔ Always verify the sender's email domain.
✔ Never click on links from unexpected delivery messages.
✔ If unsure, visit the official website directly.
✔ Use a password manager—it won't autofill on phishing sites.
✔ Report scams to your local cybersecurity authority.
📢 Final Words: To all scammers reading this: Nice try, but we’re always one step ahead. 😎